
I’m In!

I’m In!
I have followed Agent E into the Egg National Security Agency where he has gone at the bidding of Mr. Bigg Egg. To do what?
The NSA is known as the most secretive Agency within the US Intelligence Community. We know of the history of its development & it’s notable work in the field of Cryptology. Since the NSA has become involved in Digital Signals Intelligence it has become Technocratic in Intelligence gathering, which has increased in scope & size of the Intelligence gathered. It has turned its Eye upon the people of the US, upon the very Citizenry it purports to serve. The argument in support of this is that the Public must be willing to give up its Privacy in order to maintain it’s Security.
Americans are surveilled from every direction. Satellites survey us, phone calls are listened to when a negative association the Government suspects calls our line, E-Mails and all our texts and keystrokes are saved and recorded against any future or possible crime we may commit. Our Meta Data is saved and stored in huge compounds, such as the one in Utah. Fusion Centers, to monitor us are set up in all Regions and Counties in the US. Cameras and Microphones are everywhere. The NSA gathers and shares this data with 17 XYZ Intelligence Agencies and Contractors upon demand.
This out of control & illegal Spying on the Citizenry of the US is ultimately to control the populace, and as so, is Social Engineering. Otherwise it would not be to the degree it now occurs. It represses the Individual’s Right to Free Speech because of the chilling effect resultant from the Individual’s Lack of Privacy, and the feelings of intrusive violation which all Citizenry is aware of, whatever their opinions concerning this violation. We have been conditioned by Social Engineers to believe this as necessary, but is it? Do Americans really need to concede our Private Speech and Behavior to the controlling Arm, the Enforcers of Social Engineering?
I would like to understand how and when the NSA veered away from their original function of Cryptology as practiced from its beginnings during WWII and to discover when it became an Enforcer of Social Engineering.
The character of the NSA is nebulous and secretive, vague, even to it’s employees. We can not discuss, inquire, or reform this Agency unless we address not only what is known but the unknown. We must penetrate this Nebula.
All I have to do is Penetrate this Secrecy
Separate the Dark from the Light
As the song says “Thinking is the Best Way to Travel”
My Head in a Whirl, I Created a Vortex
And….
(Mother Goose on Flying With The Wild Geese)


By the end of the 19th Century, Cryptography had been rendered easily breakable, though the Telegraph had sped up the ability to transmit messages by wire. In 1896 Guglielmo Marconi filed his 1st Patent for his new invention, the Radio. Nicolai Tesla also invented the Radio but was not credited for it at the time. Signals could now be sent between two distant & isolated locations. Radio Waves bouncing off the Ionosphere, which acts as a mirror, & then off the Earths surface allowed direct communication anywhere on the planet. This was a great advantage for the Military but also a weakness because the Radio Signals could be exploited by an enemy who could now pick up Radio Waves emanating in all directions. Cryptographers had to create Codes, as they had in the past when messages were mostly on paper; to prevent the enemy from deciphering messages.
THE BLACK CHAMBER
Herbert Yardley met Ralph Van Deman when he entered WWI. Van Deman recognized Yardley’s proficiency at Code Breaking & made him Chief of the MI8 Code Section. He Commanded the MI8 Military Intelligence Wartime Cryptologic Section. Having served previously in the State Department as a Code Breaker, Yardley had amused himself deciphering incoming Telegraph Messages. He discovered there that American Secrets were easily De-Coded. His vast experience & proficiency clearly established him as one of the main experts in Cryptology.
The Cipher Bureau was created in May 1919 by the Acting Secretary of State & Secretary of War. It concentrated on Diplomatic Decrypts. Yardley, as chief of this organization, operated out of New York City. It was disguised with a Cover Operation which allegedly compiled Commercial Codes for banks & businesses.
The Washington DC Conference of 1921-22 resulting from the 5 Power Naval Treaty was concerned with limiting Post WWI activity in order to head off the Arms Race. It was at this Conference when Yardley solved the Japanese Conference Representative’s Cipher. The Cipher Bureau was very efficient & solved some 45,000 Cryptograms in a Decade. These Codes were broken by a small staff of only 20 Cryptoanalysts.
Declaring that “Gentlemen do not read other Gentlemen’s mail”, the Secretary of State under President Hoover, Henry Stimson, terminated the Cipher Bureau. The NSA, in its online Historical Papers, maintains it was shut down because of Budget concerns, while the US Government claimed it was shut down because of the need to” Act in Good Faith” since the War was over. The NSA also cites the development of the Armies Cryptologic Unit as further reason for the Bureau’s shut down. In May 1929, the Signals Corp became responsible for all Military Intelligence Cryptology.
Herbert Yardley wrote about the Cipher Bureau first in a serial form in the Saturday Evening Post, & then as a book, “The American Black Chamber”. In 1932, the book was a best seller, & henceforth the Cipher Bureau was known as The Black Chamber. Though attacked by Military Cryptoanalysts for publishing his book, Yardley defended it stating that his ” motive was only to alert the US to the weakness of its systems, & to the power of Cryptoanalysis. What he could do” he said, “people in other Nations could also do”. The Black Chamber will be remembered as the first National Civilian Intelligence Agency.
In 1929, the Personnel of the Signals Intelligence Agency which followed the Cipher Bureau were trained for Wartime Cryptoanalysis. William Friedman had been a Lieutenant in the Army during WWI, where he served in France solving German Codes. Friedman is credited for training the SIS in Codes & Ciphers using Yardley’s Black Chamber Methodologies. Soon they were studying what was thought of, according to the NSA, as the ” future of Cryptography”, the Machine Ciphers.
The SIS belonged solely to the Signals Corp & not to the Army, though they compiled Systems for the Army’s use. The SIS was renamed the Signals Security Agency (SSA) in 1943. In September 1945, it became the Army Security Agency, & was officially centralized under the Army.
DEVELOPMENT OF THE CRYPTOGRAPHIC MACHINES
The Cipher Disc had been around since the 15th Century, & Leon Alberti is credited for its invention. It was a simple machine consisting of two round plates or discs (Scramblers), with Alphabets on them. By rotating the Alphabet Discs, a Key Word could be lined up with the outer Alphabet Disc. The Key Word would be represented by the inside, or bottom disc, to encipher a message to send; while reversing the process deciphered a message.
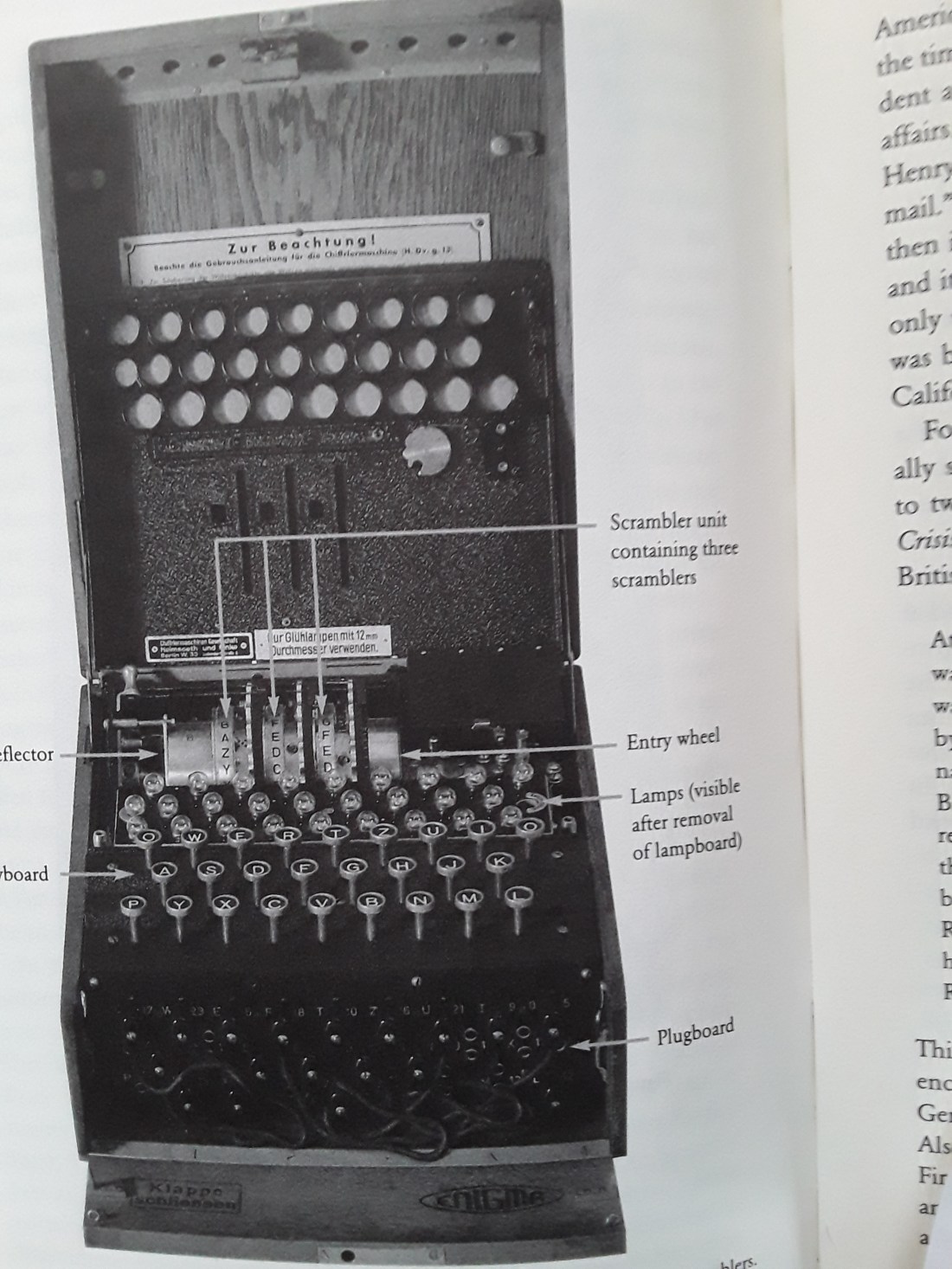
Though Pencil & Paper Encryption was used during WWI, by 1918 a new form had been created. The new Encryption Machine was invented by the German Inventor, Arthur Scherbius & was called, the Enigma. (It was called this for a very good reason, as it was quite the challenge. For years, solving it remained a mystery.). It was, practically speaking, an electrical version of Alberti’s Cipher Disc System, but with 3 Discs. The Machine’s use followed an initial commercial, & inferior version of the Enigma Machine. This was, however, too expensive for commercial purposes & cost about $30,000 by today’s standards.
During WWI a drowned German Naval Officer found on a sunken U Boat by Russian Admiralty was discovered with a German Cipher & Signal Books held in rigamortis to his chest. The Russian Admiralty de-coded a substantial portion of German Naval Messages using these Documents. The Russians relayed the Documents to Winston Churchill, who published them in his book, “The World In Crisis”, in 1923. This ability to decrypt the German Codes gave the Allies a sizeable advantage. Codebreaking, during WWI, had become proficient, yet the solution sought was in the cracking of the German Enigma Machine. Its level of Encryption was unparalleled & the most secure Cryptography in the world.
in 1931, Hans Thilo Schmidt worked for the German Command Center for Cryptology, & he passed photos of Documents with instructions on how to use the Enigma to a French Secret Agent, Code Named -Rex. When WWII started, the Allies were able to reproduce the Enigma. Messages, however, it could not be deciphered without the Key. According to Simon Singh in ” The Code Book”, “The Key was the element that turns the general Encryption Algorithm into a specific method for encryption. Though the enemy may know the Encryption Algorithm used by both sender & receiver, they must not be allowed to acquire the Key.”.
The Allies raids on German U Boats & captured Code Books gave the Bletchley Park Cryptology Department of Great Britain access to U Boat locations. The Battle of the Atlantic now favored the Allies. To prevent the Germans from becoming suspicious, since if they knew about captured “Code Books” they would change & upgrade their Enigmas, the Allies could not act on all the information that Bletchley Park had decrypted. The British had by now had sunk many U Boats & captured more Code Books, giving them access to even more U Boats. They had to let some escape. This bluff worked, & the Germans never discovered the capturing of the Enigma Plans & Code Books. The ability to break the German Code is cited as a major reason that the Allies/US won WWII. According to Sir Harry Ainsley discussing British Code Breakers during WWII, “the War, instead of ending in 1945, would have ended in 1948 had the Government Code & Cipher School (in Englands Bletchley Park) not been able to read the Enigma Ciphers & produce the ULTRA Intelligence.”. (ULTRA was the Codename for the Intelligence Operation that emerged from breaking the Enigma Cipher, & deciphering Italian & Japanese Messages.).
BLETCHLEY PARK PERSONNEL
The dedicated Personnel at Bletchley Park worked night & day solving Codes to prepare the Allies for major moves during WWII, though these preparations were kept Secret even from them. The State of Readiness of this irreplaceable & proficient Agency went unnoticed & uncredited for many years. One individual at Bletchley Park who deserves credit for cracking the Enigma, & who created the ” BOMB” to decrypt codes used by the enemy during WWII, was Alan Turing. Mr. Turing’s work was the prelude for the modern computer. Successful at Cambridge & a Fellow at King’ College, he lived the life of a noted Academic & Scholar. His work at Bletchley Park conversely, was conducted in absolute secrecy & silence. On June 7, 1954, shamed for Homosexuality & depressed, Mr. Turing committed suicide at the age of 42; without having received any credit for his important role in the winning of WWII. He had eaten a cyanide-laced apple & was found dead in his bedroom. Friends & Colleagues of Mr. Turing later recalled that 20 years earlier he had repeated the chant from a 1938 film, ‘Snow White & the 7 Dwarfs, “Dip the Apple in the Brew. Let the Sleeping Death Seep Through!”. Mr. Turing it seems was Cryptic to the very End!
All of these Codebreakers lived the rest of their lives in total & sworn secrecy until the early 1970s. Captain F.W. Winterbottom petitioned the British Government that since the Enigma Machines were no longer used, & since Bletchley Park was shut down, that nothing would be gained by hiding how Great Britain had Cracked the Enigma. The Book Winterbotham wrote, titled ” The Ultra Secret” was published in 1974, & signaled the Bletchley Park Personnel that they could “now openly discuss” their Wartime Activity. Many never discussed it, dying without giving away their Secret.
THE CODETALKERS
Though Cipher Machines & their Operators may be credited for winning WWII, one might say that “for winning the smaller battles” they were “too slow” to be entirely useful. The US Marine Corp came to the rescue with the Navaho Code Talkers. 28 Navaho Men were enlisted into the Marines & given an 8-week Communications Class. After the Bombing of Pearl Harbor in 1941, the Japanese were unable to break through the Navaho Language of either Sender or Receiver used by the Code Talkers. One might say this was a successful example of an Operation achieved by Human Sources, employing a Language used out in the open, spoken over the radio which only a handful of listeners understood, & certainly not the Japanese. One of the Code Talkers was a Navaho Man named John Pinto, who also served as a longtime Senator for New Mexico. Mr. Pinto recently passed away over the Memorial Day Weekend of 2019. Thank You for Your Service, Mr. John Pinto!
THE RED AND THE PURPLE
In 1935, the Japanese Foreign Ministry had turned to Machine Systems to encipher messages & developed “the Type A Machine” to protect communications. The Signals Intelligence Service (SIS) nicknamed the Cryptosystem “Red”. The translation of Red Messages in 1938 gave the US details of a Secret clause in the Anti-Cominterm Pact between Germany, Italy & Japan which committed each of these Countries to support the others in War, ” regardless of the circumstances.”. This turned out to be very important in understanding Japans role in WWII. The US’s close access to Japans Government Policy ended when the Japanese began to use a new Crypto Device called the “Type B Machine,” nicknamed the “Purple” by US Army Cryptanalysts.
The Japanese used both the “Red” & the “Purple” simultaneously. Though good Intelligence was collected & decrypted from the “Red”, the US still had to decipher data encrypted on the ” Purple”. The Japanese considered the encrypted data on the “Purple” to be their most important Intelligence during WWII. US Cryptanalysts discovered that the “Purple” as used by the Japanese had a weakness, which allowed them to break the Japanese Code. It seems that the “Purple” split Japanese syllables into vowels & consonants. This, & one other weakness, a Procedural mistake made by the Japanese, was a dead giveaway of their Intelligence to the US. The Procedural mistake the Japanese made was to use both the “Red” & the “Purple” Machines at the same post. They often sent the same messages at once on both systems, as they encrypted the US English Language Diplomatic Texts, easily identifiable to US Cryptanalysts.
Under the Direction of Mr. William Friedman, the solution to the “Purple” was made into a group effort. It is well documented in NSA Literature, that because Mr. Friedman liked to describe his Cryptanalysts as “Magicians”, he established the Code Word ” MAGIC” to mark his decrypts since they required special protection. In January 1941, by agreement, only 10 people had access to “MAGIC” Translations: The President, The Secretaries of War, Navy & State Chiefs of Staff, The Chief of Naval Operations, The Chiefs of the 2 Services, The War Plans Division, & The Chiefs of their Intelligence Organizations. “No Decrypts were distributed outside of the Continental US,” according to the NSA.
The NSA has a Note on their Web Page: “In the middle of WWII to avoid confusion the US adopted the British term ” ULTRA” for most decrypted Intelligence for High-Grade Systems; the Code Name “MAGIC” survived for daily summaries of some high-level Decrypts.” (NSA)
After the SIS solved the “Purple”, an SIS Electrical Engineer named Leo Rosen produced a Prototype for the SIS version of the ” Purple” which was called the “Purple Analog”. The Navy built 3 “Purple Analog’s” in its own facilities; they sent one to the Army & kept one for itself. The 3rd Machine was sent to Great Britain since the two Countries had co-operated closely in the Cryptologic effort during WWII.
THE COLOSSUS
The Invention of The “Colossus” Machine by Great Britain’s Max Newman & perfected by Tommy Flowers proved a revolution for Cryptology. Consisting of 1500 Electronic Valves, rather than the Electro-Magnetic Switches of early Wartime Cryptology Encryption Machines, The Colossus was much faster. The Colossus was the first Programmable Computer. The Colussus Blueprints were destroyed after War II, so others received the credit for its invention. Secret during the War, perhaps after the War the intention was simply to respect that Secrecy & so, it was kept Secret. This was part of the Distinction deliberately made between Wartime & Peacetime Surveillance Activity, unlike today. There was a Distinction between Foreign & Domestic Surveillance at the time but it was generally unquestioned by a Civilian Populace. The idea of a Government Spying on its own Citizenry was rare, given the Public Attitudes which did not acknowledge a never-ending War, with a front encompassing the entire World.
Since the time of the Colossus until today, the use of Computer Technology entirely changed Cryptology. The Computer was faster & could mimic the actions of hundreds of scramblers, unlike the mechanical Cipher Machines; & it scrambled Binary Numbers, rather than Alphabets.
FROM THE SIGNALS CORP TO TODAY’S NSA
In May 1929, the Signals Corp held a 2-week Training Program in Cryptologic work for Officers. Units were established to compile codes, to train to solve enemy codes in “times of War & to establish Intercept Services in the field.” (NSA). The Signals Corp interpreted the work of the Signals Intelligence Service, which was a part of the Signals Corp. The NSA stated the declaration of the Signals Corp mission: “All work of the Signals Intelligence Service (SIS) is to be organized on the basis of training for War, rather than that of Active Operations for immediate interception & solution of the Communications of foreign Armies & Governments.” (SIS/NSA). They did however, accept such data if it became accessible during training.
Trained by William Friedman, the Signals Corp stressed Cryptanalysis. The main duty was to compile Codes for Army use; however, Friedman’s training in Ciphers & Codes was rigorous. They were also made entirely familiar with Yardley’s Black Chamber Foreign Systems & Methods for solving them.
The Signals Intelligence Service was not attached to the Army but was Civilian. Military Intelligence considered Cryptanalysis an adjunct of Cryptography, & a part of the Signals Corp. The SIS’s duty was to compile systems for Army use, & to prepare Cryptanalysts for Wartime Operations. Their purpose was not conducting Foreign Intelligence. “The SIS was renamed the Signals Security Agency in 1943, & in 1945 became the Army Security Agency.” (NSA). The National Security Agency (NSA) became it’s own separate & independent agency in 1952.
During WWII the Signals Corp focused on Codebreaking & Code Cracking, especially Japanese Codes. As it developed under the Army & later as the NSA the focus was on Signals Intelligence, or SIGINT, the intercepting & processing of Foreign Communications (not only during Wartime), Cryptanalysis or Codebreaking, as well as Code Sending or Cryptography. Currently the NSA has expanded its Operations inside the USA, & onto US Citizenry, & includes “Surveillance Operations & Information Assurance.” (NSA)
FINI


XYZ Intelligence Agencies have a History of acting both inside and outside of their Agencies; collectively, and as individual Agents. These Agencies have acted under the Laws, Regulations, and Authorizations of the US Government, and outside of them. What happens when Federal Law Enforcement separates from the Government and the Country it proposes to work for, and goes Rogue? Though Rogue, it is important to understand that individuals within these agencies invariably work for someone. It is clear, that in many cases this Intelligence personnel have ceased to work for the American Citizens, who, according to the US Constitution ARE the Government.
The Exploration of the current, as well as the past behavior of XYZ Intelligence Agencies, is necessary to understand at what point in History these Agencies stepped away from their original Agency Mission as stated in their Official Mission Statements; in order to engage in the Social Engineering of Citizens within the Nations they once served. How, and when did XYZ Intelligence Agencies become Enforcers of Social Engineering? What were the effects within Societies Enforceably Engineered? I maintain that Social Engineering as Enforced by XYZ Intelligence Agencies can only harm our Nation and the American Citizenry which they now attempt to Control. Within the context of my writing this Author hopes to delineate these effects.
In 2004 the Office of Director of National Intelligence was established, under the Directorship of John D. Negroponte. James Clapper was the Director under President Obama. The current Director is Daniel Coates, who was sworn in on March 16, 2017. He serves as the principle Intelligence Advisor to President Trump. The Office of Homeland Security also Advises him. The ODNI co-ordinates and collaborates the Data it collects with all other Agencies. The NSA and the CIA also collect and distributes Data across Agencies. The DOD and Defense Intelligence Agencies are Authorized to work somewhat independently, however. President Obama merged all these Agencies together. Some Reports indicate that the CIA and NSA had been merged together for a long time unofficially; and that the FBI was brought into this merger in 1999. In 2011, President Obama expanded the NSA to allow this Agency Official Authorization to collect all Data and share it with all other XYZ Intelligence Agencies. Currently, the other Agencies can apply to the NSA for Raw Intelligence and review it before implementing any Privacy Restrictions. Previously, the NSA actually did apply a certain amount of Privacy Restrictions before sharing Data with other Agencies. Signed in 1981 by President Reagan, Executive Order 12333 was required to make any determination about applying Privacy Rules. Since then, it has been amended 3 times. Currently it is not required to apply for this Order when sharing Data between Agencies.
Again, what are the effects of the merger of XYZ Intelligence Agencies? This question is of major concern, especially when we come to understand that these Agencies have no obligation to apply Privacy Restrictions when sharing Information between Agencies. The Surveillance Capacity of the XYZ Intelligence Agencies is now increased with both Agency Merger and Sharing of Data; and since the number of Analysts is increased by the merger between 17 XYZ Intelligence Agencies, as well any number of Sub-Contractors and Detailees, Data on Individual Americans and all their Associations, and Associations association can be spread throughout the Agencies to sift through. The use of Incidental Information may be used on any American by any Agent simply stumbling over such Data. This now applies and connects Data from anywhere in the World, Foreign or Domestic. Since the Data is so widely disseminated it can also be hacked easily by expert hackers foreign or domestic. The Vast Data storage the NSA maintains in Utah is also widely accessible. Many of the Foreign & Domestic Companies have created back doors into cell phones, Computers, and other Technology. Incidental Information can be used to create Criminal, or Counter Intelligence Investigations with or without a warrant under the National Defense Authorization Act (NDAA).
There may be Rules, Regulations, and Laws meant to ensure Citizens Privacy will not be violated, and that the massive potential for the Abuse of Power these Agencies wields will not endanger Citizens Privacy, but I fail to see how these Rules, Regulations and Laws can be maintained without Checks. From 2016 to 2019 alone there has been massive evidence made public to American Citizens of Abuse of Power by XYZ Intelligence Agencies. The effects have shown a Surveillance State with no bounds and no real oversight. Though Congress, with their Over Sight Committees attempt to bring the Agencies to Account, so far, and perhaps, through no fault of their own, they have failed in this endeavor. However, we have also witnessed an extreme Politicization of these Agencies who definitely have their connections in Congress; those who simply and knowingly turn a blind eye to the Abuse of Power, and merely Wink. Such XYZ Intelligence Agencies are supposed to be Non-Partisan and to check their Bias’ at the door, but when collaborating with Politicians and Media, and having no bounds or Accountability; they have become the Unelected Governors of a Nation and Enforcers of Social Engineering.
The merger of the XYZ Intelligence Agencies potentially allows a small group of Rogue Agents to Collect and Share Data gathered by the Agencies, and to use the Data outside of their Agencies. This is especially dangerous since many of the Top Cops within the XYZ Intelligence Agencies combined have the power to De-Classify Data, move it, and even to Leak the Data without penalty or observation. We have seen this occur during the period from 2016-2019. Hillary Clinton’s Dirty Dossier of Russian Propaganda gathered by Foreign Agent Christopher Steele managed to end up in a whole gamut of locations in this manner. An Agenda separate from the Government was pursued to the detriment of our Countries Rule of Law and Constitution, in this instance. I will not go into all the details though I have discussed it previously; and, it is all over in the Public Record.
When Data can so easily be moved around throughout XYZ Intelligence Agencies, can Investigations relegated to Foreign Countries (as once was the case for the CIA) be relayed back to any Intelligence Agency within the United States? Yes. What happens when this Data is used by a small group of Politicized, or Rogue Agents in order to pursue their own Agenda? I maintain that this has been occurring periodically since the establishment of the XYZ Intelligence Agencies regardless of Rules, Regulations or Law. The Public, of course, is told otherwise. This Author, in future writings, hopes to delineate this subject.
Between 2016 and 2019: and during the Presidential Campaign, Candidate Trump, and then President Trump was made a Target by the XYZ Intelligence Agencies. This too is in the Public Record. The Unconstitutional Targeting and Harassment, and Soft Coup attempt on the President continues to this day by the Top Cops of the various XYZ Intelligence Agencies who served under President Obama. Many have left or have been fired for their Nefarious, highly coordinated and Organized Mis-Behavior, yet many individual Agents involved, remain and continue to act against the President of the United States, and of course by doing so, Act Against the Citizens of this Country. Do they know what is best for We the People? They certainly never asked us!
As an Executive Order, Executive Order 12333 can be changed, reformed or reapplied by our President. It has been amended three times. I suggest it is a good idea that the Order be Revised and Reapplied. From my viewpoint, as a Citizen, the methodology of the XYZ Intelligence Agencies and the Department of Justice has been dysfunctional.
The FISA Court is supposed to not only Uphold our Rule of Law but Protect Citizens from Governmental Abuse of Power. In the 2 Tier Justice System we now live under, the FISA Court has stopped asking the pertinent questions needed to protect Citizens from Governmental Abuse of Power. I cite the case here of Carter Page. The FBI applied for a Surveillance Warrant on Mr Page while he worked on the Trump Campaign and then of course, proceeded to Surveille him, and everyone else who came into contact with Mr Trump. FBI claims that they only surveilled a small number of individuals but with incidental and associative surveillance. With the sharing of Data, how could it not have involved several individuals though claimed otherwise? This was done to gather incidental Data on our President before and after he was elected. The FBI and DOJ signed off, approving the Warrant four times. Though the FBI had claimed under James Comey that the document, which the Warrant Request was based, was both Salacious and Unverified, the fact that it was gathered and paid for by Opposition Candidate Hillary Clinton using a Foreign Agent and Russian Propaganda was never questioned, nor were the dots ever connected by the FISA Court. The Surveillance Investigation went forward. The FBI, the DOJ Deputy Attorney General Rod Rosenstein, all were complicit in Crimes against the US, and for which there is ample evidence; these Agencies, along with the FISA Court could not be counted on to Protect American Citizens!
The FISA Court with its reputation for Rubber Stamping Warrant Requests by Agencies having shown no loyalty to a Government and Constitution they once served endangers all Americans, and this Court MUST be Investigated for the results of their Actions which has rendered valuable Protections of American Citizens ineffectual. How can Congress oversee what is held Secret by a small group of Rogue Agents who are no longer working for the US? Congress, I must say does try, yet cannot and has not succeeded.
Though individual XYZ Intelligence Agencies are, according to US Law required to provide formulaic written Justification for their Activities, I question whether this Justification always takes place. I believe that on some level it must & needs to be, if Order and Ethical Practices are to be maintained, but this is not the case. As stands, I don’t think their behavior, whether Historical or Current, can in fact be Justified, since it is based on Defiant Reason, Outside of Ethical, and Outside of Agency Precepts, and Mission. So, they are, again, not Justified. If, after all, as often and as is currently the case, Citizenry have been overpowered and dominated by a Police Surveillance State, whose goal is Control of a Populace, just who would they feel they are responsible to? Who, in this case would Agents feel the need to Justify their Behavior, Investigations, Analysis and Data Collection to, much less have a need to Inform them, or make Predictions based on Analysis to be included on the Public Record? Certainly, the motivation would not include Representatives of We the People! Top-level XYZ Intelligence Personnel with the power to DeClassify can acquire more Information/Data on Citizens by this mismanagement of Agency Data and Process. Many Citizens are caught up in the Net of Raw Signals Intelligence Investigations with Data acquired Incidentally or by Association. Is new Authorization given for each and any Citizen whose Data is collected this way? No, it is scooped up completely and immediately.
Even if Executive Order can be 12333 can be Controlled or Cancelled by the President, what happens if a group or Cabal forms within XYZ Intelligence Agencies and decides to Re-Classify, or move Data to a different file? Does, in this case, Executive Order 12333 still apply? How haphazardly can Data be shifted and placed under Supervisory Control outside of the Executive? This indeed does happen and continues to happen.
A number of Top Level XYZ Intelligence Agents of the Obama Administration no longer serve in the Administration of the current President Trump; and unfortunately, nor do some of them even serve the US though they still engage in Intelligence work. Why would these ex Agents, or the Agents still working for their Agencies bother to adhere to any Regulations still Governing their behavior? Many overtly violate the Laws of the US without considering Authorizations, Classifications, Laws and Regulations, though the Public is told differently. Are they Self Justifying their off the Record behavior?
The subject matter of XYZ Intelligence Agency History of Social Engineering is so large that my purpose cannot be to cover each Agencies Historical and Contemporary Social Engineering; but in contrasting the original purpose and mission of the major Agencies, I hope to come to an understanding of how and why they became Enforcers of Social Engineering outside of their initial missions.
What is the effect and implications to the Society in the US who are under the Control Mechanisms of XYZ Intelligence Agencies or Agents who have broken away from our Government and Constitution they once served? This is not to negate the ‘raison d’etre of these Agencies, but is an inquiry, and attempt to demonstrate that XYZ Intelligence Agencies endeavor to Control the Populous of the US through Social Engineering and outside the scope of their initial establishment and mission; and, that it is Unethical!